Secure Multiparty Computation
Project guided by Prof. Sibiraj Pillai, Prof. Vinod Prabhakaran, Prof. Manoj Prabhakaran (as B.Tech. project)
Link to B.Tech. Project thesis
Link to publication
Abstract — In an influential work aimed at understanding the communication requirements of secure computation, Feige, Kilian and Naor introduced a minimal model of secure computation (STOC 1994). In that work, among other results, Feige et al.\ presented a simple protocol for the 2 input AND function. It has remained an intriguing question whether the communication and randomness used in this protocol are optimal. While previous work of Data et al. (CRYPTO 2014) showed that the communication from the two parties with inputs (Alice and Bob) to the third party who gets the output is optimal, the question of optimality for the third message in the protocol – a common reference string shared between Alice and Bob – remained open. In this note we show that in fact, this message (and hence all the randomness used in the protocol) is also optimal in the protocol of Feige et al. This improves on a previous result of Rajan et al. (ISIT 2016), which showed this optimality restricted to protocols where Alice and Bob are deterministic. Further, our result holds even if only a weak secrecy condition is required of the protocol.
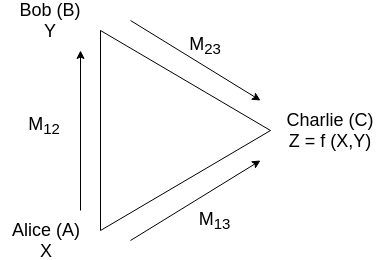
An illustration of the three-party secure computation problem